Biometrics are a powerful solution to identity authentication: but they also escalate the risks of data breaches into the realm of catastrophe: here’s how to solve the problem with decentralized identity and verifiable credentials.
By Trevor Butterworth
You can’t reset a person. That is, cosmetic surgery aside, you can’t reset the physically distinguishing and unique characteristics that make us who we are.
Which isn’t a problem, unless you create an identity system based on using these characteristics — aka biometrics — to authenticate access to high value information like bank accounts.
And, of course, that’s just what we’ve done. To address the inherent weaknesses of passwords, we’ve turned to deeper, probabilistically unique, identifiers like facial recognition, fingerprint scans, iris scans, and behavioral and vocal recognition.
In one important way, these are much better ways of authenticating access than passwords and pin codes simply because they are unique to the person seeking authentication. They provide confidence that a person is who they say they are in a way that passwords never could. They are also fast and approach the seamless interaction that people desire and systems require.
The way biometric data is stored should scare you
But in one critical respect,biometrics are much worse than passwords: they can’t be reset.
The way biometric data is used requires comparing a real-time scan of a particular biometric characteristic against stored data for that characteristic.
Therein lies the first of two problems: if the biometric data is stored in a centralized database, the risk of a data breach will never be zero. And if there is a data breach, it’s a privacy and security catastrophe. Fraudsters have access to your unique characteristics.
Now guess where biometric data are conventionally stored.
“Bring your own biometrics”
Verifiable credential technology provides a simple fix: it removes the need for centrally storing biometric data in order to facilitate authentication.
Instead, during onboarding, a person’s biometric data is captured by a relevant authority (e.g., a bank) in a biometric template. This biometric template is then issued as a verifiable credential, which the person holds in a digital wallet.
The credential is a unique cryptographic proof that their biometric data has been authenticated by the given authority. As the biometric data recorded in the template is digitally signed, any attempt to alter it will render the credential non-functional.
When the person performs a biometric scan, they also present their biometric template credential. Because of the way these presentations are made, only the person issued with the credential can present their credential. The biometric template in the credential is cryptographically verified as authentic and compared to the biometric scan.
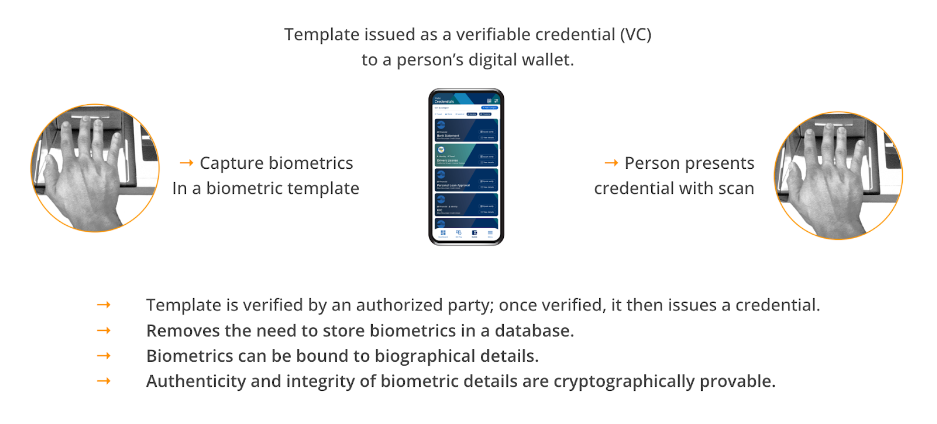
In this way, a person “brings their own biometrics” for authentication. The source of the credential is verified by the relying party — e.g., a bank can cryptographically verify that it had issued you and only you with this biometric credential, while digital signatures show that the biometric data has not been tampered with.
With no more than a couple of screen swipes, the problem of centralized biometric data disappears, and with it the nightmare of data privacy and protection and compliance.
In our next piece, we’ll look at the second problem with biometrics and authentication: how verifiable credentials can defend against the challenge of generative AI deepfakes.
If you would like to see how you can easily get started with this technology you can learn more about Indicio’s full solution for decentralized identity, Indicio Proven®.
If you have questions about how decentralized identity could apply to your organization our team would be happy to discuss it with you. You can get in touch or book a demo here.






