A simple overview to help you understand what governance is and how it applies to decentralized identity and verifiable credential technology, and what you need to think about in order to build and deploy solutions.
To stay updated on all things governance, sign up for the Indicio Governance Newsletter.
By Trevor Butterworth
Decentralized identity governance covers both the traditional remit of governance — who is in control and therefore accountable — with the technical policies, rules, and procedures that apply to any given use of decentralized identity.
This hybridity can be a source of confusion. Those from the business world may think in terms of corporate governance and those from the engineering world may think in terms of technical stacks. In merging the two, the goals of clarity and simplicity — hallmarks of good governance — run into the complexity of technology, which in the case of decentralized identity, is compounded by its recent emergence, protean capabilities, and unfamiliar concepts and terms.
Our goal here is to simplify and help you understand the basics so that you can start implementing the technology.
Getting started
Let’s assume that you’ve already decided that you want to use decentralized identity and verifiable credential technology to share and verify data without the need for direct integrations or third parties.
To implement your solution, you need to ask yourself/team/partners the following question: Do you want to—
create an ecosystem of your own (by ecosystem we mean a complete system for issuing, holding, and verifying credentials/data/identity for a specific use case)
or
only issue credentials on an existing ecosystem
or
only verify credentials on an existing ecosystem?
Answering “yes” to the first means you are the governance authority (or you and a partnering organization or government will co-create the governance if the solution has multiple stakeholders).
A “yes” to the second or third means you need to evaluate the governance of the ecosystem you’re joining to see if it meets your needs.
Additionally, if you are creating an ecosystem and the use case comes with a regulatory requirement to run your own verifiable data registry/distributed ledger network, you’ll need to create network governance.
The image below illustrates the decision process.
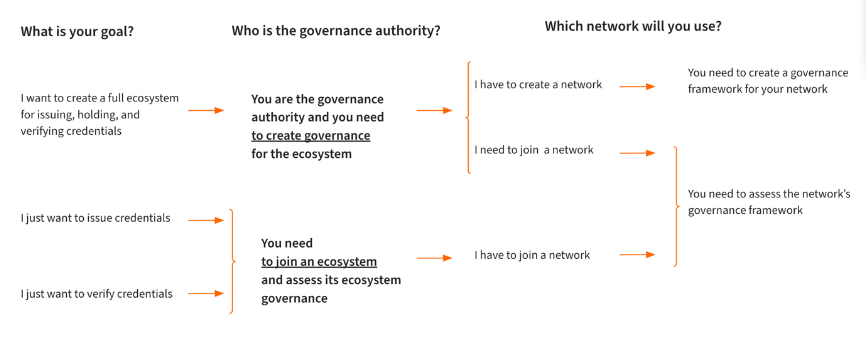
One thing to note is that most solutions do not require creating and running your own verifiable data registry/distributed ledger network. There are global networks to choose from, including the Indicio Network, which is purposefully designed for enterprise grade solutions. The point is not having to create a distributed ledger network radically simplifies the amount of governance you have to create and manage, something that’s not always apparent.
One solution, three governance elements,
For the next step, we’re going to borrow a visual aid from St. Patrick, a shamrock. Right now, any implementation of decentralized identity is going to have the following governance elements.
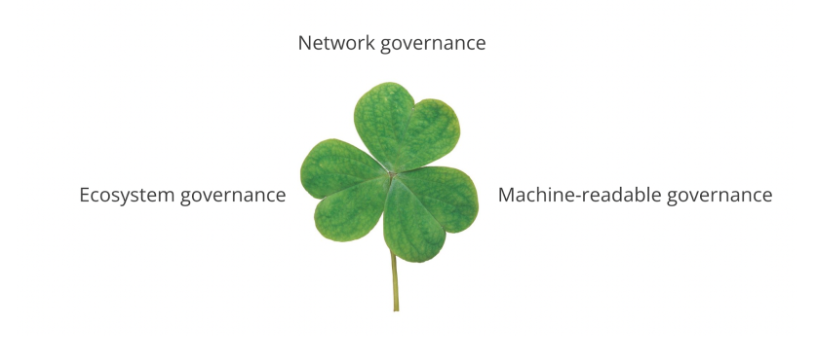
Ecosystem governance applies to the Issuers, holders, and verifiers of verifiable credentials. A governance authority establishes rules for participation and interaction. If you’re creating an ecosystem, as we’ve noted, you are the governance authority for all these participants.
Machine-readable governance is a way to encode ecosystem governance rules — that is, who is a trusted issuer, what attributes must be presented — in a file that agent software (the software used by issuers, holders, and verifiers) can access and cache. It enables human governance rules to be automated. And because the rules are cached, credential verification is possible in offline situations.
Network governance comprises the governance for a distributed ledger network, which includes the legal agreements for credential issuers to write to the ledger. As noted, you’re unlikely to need to create this, but you will have to evaluate other networks based on their governance and, if issuing credentials, you’re likely going to have to sign agreements to write to a network.
What are the key governance issues in each of these elements?
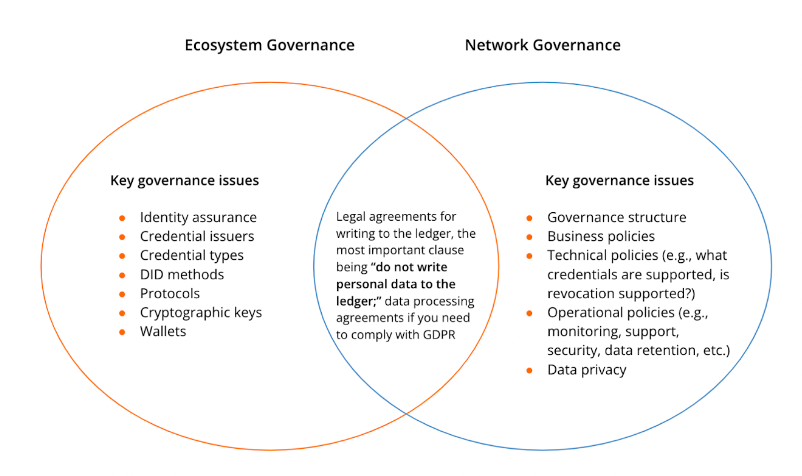
To implement governance, you are going to have to make a series of policy and technical decisions on each of the bullet points in Ecosystem Governance, and evaluate competing networks on the bullet points in Network Governance.
Here are some of the important decisions you are going to have to make when creating governance for an ecosystem
Identity assurance — are you issuing credentials to people, organizations, or things? How much information in the credential will identify the person compared to describing the credential? For the personal identity attributes, do you need an identity assurance process?
Credential issuers — Will there be multiple credential issuers in your ecosystem? If so, how are they to be onboarded?
Credential types — what credential type should you use for people, organizations? Do you need selective disclosure? What are the policies and procedures for credential expiry, revocation? Are there any restrictions on who can verify credentials?
DID methods — What DID methods for which participants? Should you use a DID method with communication endpoints? How much durability do you need in your ecosystem?
Protocols — Do you need secure protocols for notification and confirmation? What device capabilities will your participants have?
Cryptographic keys — How will you manage key rotation?
Wallets — What are your options and requirements? Do you have a recognizable brand?
Networks — Will you use a network? Which one will you choose and how will it benefit your solution? (Learn more about the networks Indicio offers and how to choose the best one to fit your needs.)
This is not an exhaustive list of things to consider or the place to dive in and provide analysis and recommendations. But looking at these issues and making decisions is not an Everest-summiting task. In all likelihood, you will make them in consultation with one or more partners who will likely have specific requirements.
The net result will be a set of approved credential issuers (a trust list) and a set of rules for interaction between all participants.
We strongly recommend encoding these rules in machine-readable files that can be downloaded by each participant in the ecosystem/use case. Why? It’s simple, it’s flexible, it makes governance portable — and it has provided the best solution for our customers (we’ve created a governance editor to help automate the process).
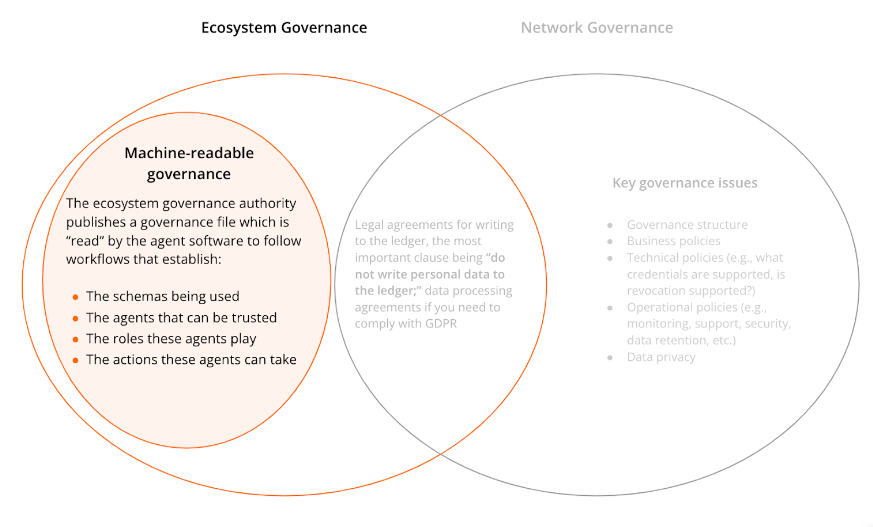
Those are the basics. You should have a broad idea of what you need to address in order to implement or evaluate governance for your solution. It’s the starting point for understanding the decisions you need to make, and we’ll cover those decisions in future blog posts.
If there is one thought to end with, it is to choose options that provide the most flexibility for future development. Technology is not static and with something as powerful as verifiable data, the only thing you can be sure of (besides the data) is that people will innovate in ways that cannot be anticipated. We always recommend building solutions that are capable of managing multiple credential formats, easy key rotation, and (quite essentially) provide communication endpoints so that you won’t find yourself at a sudden competitive disadvantage.
To stay updated on all things governance, sign up for the Indicio Governance Newsletter or contact us or learn more about Indicio Proven®, our complete verifiable credential solution with simple, built-in, easy-to-use governance.






