By Sam Curren
Trusted communication continues to be the internet’s critical missing component, even as our reliance on digital services like healthcare, mobile banking, and payments increases and where seamless, secure interactions are vital. While there are some applications and protocols designed to try to foster secure communication, they are narrow in scope and fail to broadly support the diverse types of communication we need. This shortcoming stems from their fragmented abilities and limited scope. They focus on specific areas of communication, such as simplifying complex login procedures or various security schemes, but they fail to allow the kinds of communication necessary for a variety of online activities.
The result is an incomplete tech landscape, where direct, secure communication is not fully achievable, where users are left with a fragmented landscape of partial solutions, and a successful zero trust security practice continues to challenge even the most well-resourced organizations. Without holistic and user-friendly solutions that address these shortcomings, true, trusted, general communication on the internet remains an unfulfilled promise.
This is why more industries than ever are turning to decentralized identity and verifiable credentials to solve these missing pieces and why we’ve built DIDComm into the heart of Indicio Proven. While many other standards and protocols are developing to support the simple exchange of information using verifiable credentials, the vast majority of customer use cases that Indicio supports require both sides to authenticate, communicate, and build using the existing infrastructure they’ve already invested in. You can see deployments in travel, financial services, government and more.
The success comes from DIDComm
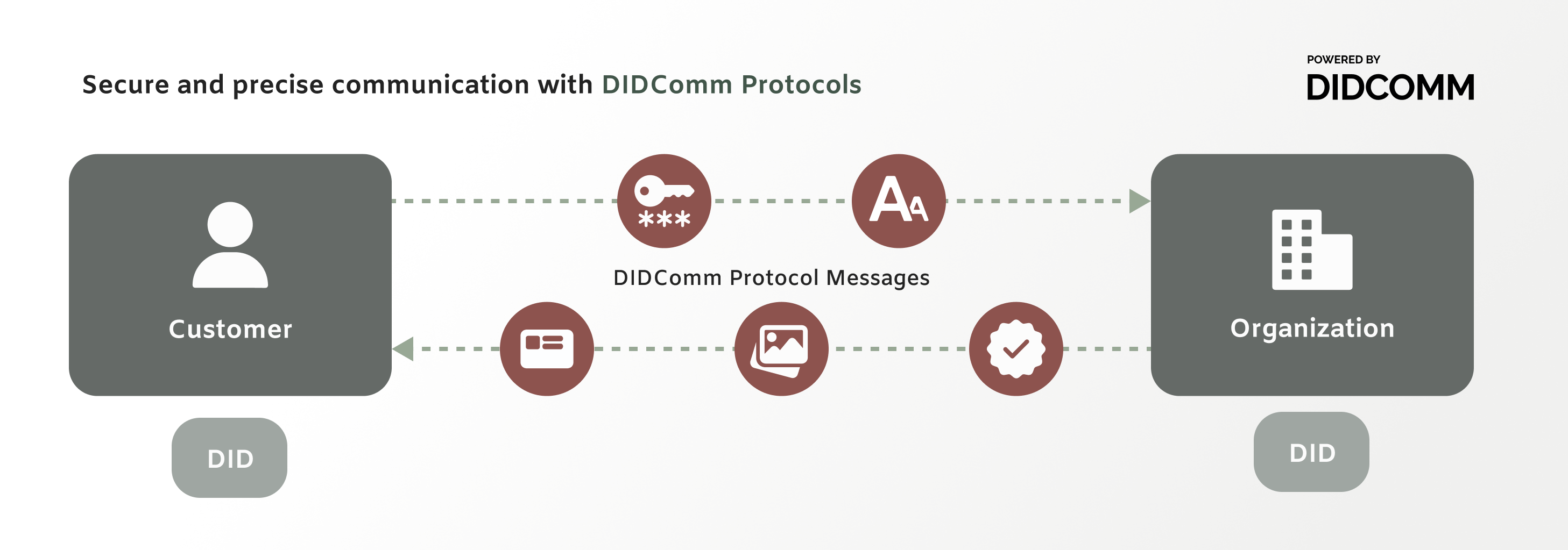
DIDComm, or DID Communication, is a protocol designed to enable secure and private communication between parties by using decentralized identifiers (DIDs). Unlike traditional methods for trusted connections, DIDComm provides a robust framework for mutual authentication and trusted communication, addressing the gaps in current technologies. DIDComm leverages Verifiable Credentials to add trust to long-term digital relationships. By integrating DIDComm into an existing tech stack or ecosystem, both end users and businesses benefit from enhanced security, privacy, and trust.
For end users, DIDComm ensures that the communications they have with each other are not only encrypted but also authenticated. This means they are secure from malicious actors impersonating them but also impersonating the business or other entity they are communicating with. This benefits businesses and governments by facilitating secure and seamless interactions with customers, partners, and citizens, while reducing the risk of impersonation, mitigating fraud, and enhancing trust.
The decentralized nature of DIDComm also means there is no reliance on a central authority, organization, or company to manage the process or facilitate identity (anyone can use software to create a DID with an endpoint for DIDComm and cryptographically prove they control their DID). This increases resilience and reduces security vulnerabilities with a zero trust enhanced architecture.
Incorporating DIDComm into your digital identity strategy is a game-changing move as it means that all parties in an identity ecosystem or communication channel can confidently authenticate each other and exchange information securely. This removes a fundamental weakness in current identity verification and communication.
The value of DIDComm lies it its ability to enable:
Secure communication: Traditional forms of digital communication, such as email, are often not encrypted at all, likely passing in plain text, meaning anyone who can observe network traffic can read it. And while email can be helpful as it serves both as an identifier and a method to communicate, the lack of secure, easy-to-use encryption creates security vulnerabilities when it comes to relaying sensitive information, such as health and financial records. While there are ways to encrypt email, they are typically clunky and not user-friendly. DIDComm solves this security problem in a way that is user-friendly, offering seamless key management and encryption.
DIDComm also fulfills the need to communicate securely while authenticating the identities of the participants. It requires an identifier that is verifiable and adds the ability to communicate both securely and privately.
Direct connection: DIDComm changes the nature of how we interact online, allowing us to regain the ability to communicate directly with others on the internet without dependence on third party platforms. This direct connection restores the security and trust that were lost with the reliance on intermediaries, such as email clients or social media platforms.
Extensibility: Much like the internet itself, DIDComm is highly extensible. It can be enhanced with capabilities through the design of new protocols. This extensibility allows DIDComm to interact with various things, people, and systems, making it incredibly useful. And where APIs are convenient ways to build complex communication protocols into online interactions, they require constant connection between their source and the end user making them difficult to update and manage, especially if connectivity is lost. DIDComm is optimized for, and extremely compatible with, commonly used devices such as mobile phones and tablets.
Mutual authentication: Authentication from one side of a connection, which many traditional digital identity tools are capable of doing, is not enough. Both parties must be able to verify each other’s identities for there to be truly secure communication. But mutual authentication is rarely straightforward and often requires cumbersome setup and maintenance, which can deter widespread adoption. Applications and protocols also overlook the need for comprehensive privacy measures, failing to protect metadata or ensure data integrity across all layers of communication.
DIDComm enables mutual authentication, providing assurance to both parties in a communication channel that they are who they claim to be. While many existing systems authenticate one side of a connection, such as just identifying the customer or end user, it is equally important that the other side is also authenticated. Think about the phishing scams where fraudsters pretend to be your bank or other service in order for you to share your login information with a bogus website or login portal. DIDComm eliminates this. You’ll always know you are interacting with your bank.
Protocol interoperability: DIDComm can also be used alongside more focused protocols, such as OpenID4VC (which is limited to only the exchange of verifiable credentials and doesn’t provide a generalized method of communication). DIDComm goes beyond single purpose protocols and combines the power of verifiable credentials with extensible communication. The trust gained by the exchange of verifiable credentials can then be used to coordinate powerful interactions, secure messaging, and more.
Until DIDComm, the internet has been missing an easy, comprehensive solution for secure and trusted communication. Applications and protocols built on DIDComm support use cases ranging from communicating with government border authorities for the preclearance of international travelers to businesses and financial institutions offering customized products to customers.
To get involved with DIDComm, individuals and organizations can participate in the work of the Decentralized Identity Foundation (DIF), contributing to the development of standards and protocols, collaborate with industry leaders, stay informed about the latest advancements, and help shape the future of decentralized identity and secure communication.
Indicio has extensive experience with DIDComm, and we’d love to help you integrate Indicio Proven into your existing systems. Reach out to Indicio and learn how DIDComm can empower your organization.






