Traditional identity providers allow you to configure access across your organization in a variety of ways, including passwords, multi- factor authentication, or logging in with a google account. Proven Auth adds a fourth option in the form of tamper-proof Verifiable Credentials for a faster, more secure login experience.
By Tim Spring
Proven Auth is a version of Indicio Proven designed to enable single sign-on (SSO) using Verifiable Credentials. Proven Auth is more than just a way to enable passwordless authentication, it is a system for orchestrating access to applications and resources and managing the lifecycle of a user so that they have access to what they need — and only what they need — when they need it.
For example, Proven Auth can be used to issue employees with Verifiable Credentials for access to applications and documents or even to the areas they need access to based on their role within a company. A sales team member would have access to sales resources that an engineer would not. Or when an employee changes teams, their access can be immediately updated in the system’s governance file. If they leave the company, their credentials can easily be revoked, so no more collecting key cards or changing passwords.
Why login with Verifiable Credentials?
Verifiable Credentials offer benefits that traditional login systems simply cannot compete with.
- They remove the need for logins and passwords and multi-factor authentication. We’ve said it before and we’ll say it again, any system that relies on usernames and shared secrets (passwords, security questions, etc) is vulnerable to data breaches and impersonation attempts.
- They can be verified without phoning home or checking in with a third party. Credentials are verified through cryptography. You can be certain who issued the credential and that the information in the credential hasn’t been tampered with. This means that personal data doesn’t need to be stored in a centralized database to confirm who you are, and you can prove your identity instantly to the system without needing to check in with the issuing party or a third party identity provider.
- They stop account takeovers and impersonation attacks. Each Verifiable Credential is bound to its owner and stored locally in a digital wallet app on their mobile device. Access to the wallet and device are through biometrics and code. The credential can’t be shared for someone else to use, it can’t be faked, and it can’t be stolen.
- Easily implement least-privilege access. Verifiable Credentials simplify applying zero-trust approaches to security. With Proven Auth, you configure governance files to orchestrate who has access to what. It’s authentication plus access management.
How do I integrate Proven Auth into my existing identity provider’s systems?
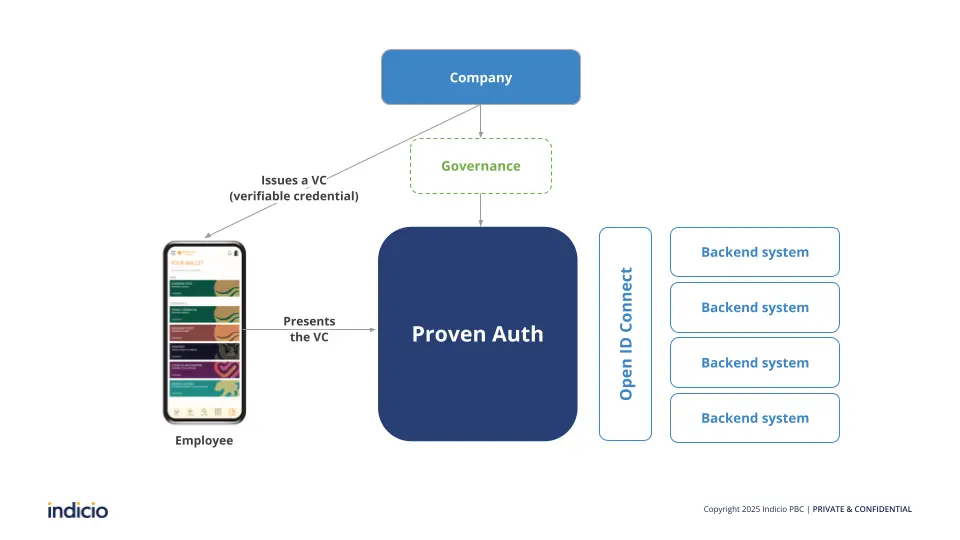
Once you have Proven, our team at Indicio has created a collection of APIs that will allow you to access the option for Verifiable Credentials the same way that you can access any other option when logging into your systems, such as an existing user account.
Once you have integrated Proven Auth into your systems you will see the option to issue credentials to users, who will be able to hold them in a digital identity wallet, and share them back to your system for verification.
A full demonstration of integrating Proven Auth and what the new user experience will look like can be found on the Indicio YouTube Channel.
How do I get started?
Getting started is as easy as reaching out to the team at Indicio to discuss your current systems.
Our team has years of experience creating solutions all around the globe, and will make sure that your team can not only integrate Verifiable Credentials quickly, but is set up to get the most use out of this powerful technology. If you’re not quite ready to speak with them yet, we encourage you to explore the Proven Auth solution brief.